- Apply for Authority
- P-ISSN2287-9099
- E-ISSN2287-4577
- SCOPUS, KCI

A Design of Secure Communication Architecture Applying Quantum Cryptography

Yong-Hwan Kim (Korea Institute of Science and Technology Information (KISTI), Advanced Quantum KREONET Team, KREONET Centre, Daejeon, Korea)

Wonhyuk Lee (Korea Institute of Science and Technology Information (KISTI), Advanced Quantum KREONET Team, KREONET Centre, Daejeon, Korea)

Abstract
Existing network cryptography systems are threatened by recent developments in quantum computing. For example, the Shor algorithm, which can be run on a quantum computer, is capable of overriding public key-based network cryptography systems in a short time. Therefore, research on new cryptography systems is actively being conducted. The most powerful cryptography systems are quantum key distribution (QKD) and post quantum cryptograph (PQC) systems; in this study, a network based on both QKD and PQC is proposed, along with a quantum key management system (QKMS) and a Q-controller to efficiently operate the network. The proposed quantum cryptography communication network uses QKD as its backbone, and replaces QKD with PQC at the user end to overcome the shortcomings of QKD. This paper presents the functional requirements of QKMS and Q-Controller, which can be utilized to perform efficient network resource management.
- keywords
- secure communication, quantum key distribution, quantum key management system, Q-controller, post quantum cryptograph, quantum cryptography
1. INTRODUCTION
Existing network security methods are at risk due to the development of quantum computing. The Shor algorithm, which can be run on a quantum computer, can endanger the security of RSA (Rivest-Shamir-Adleman) public key cryptography systems in a short time (Arute et al., 2019; Shor, 1994). Therefore, studies on quantum key distribution (QKD) and post quantum cryptography (PQC) are being conducted to improve existing network security methods and prevent network threats caused by quantum computing. QKD is the most powerful security method because it can use quantum properties to detect eavesdropping by attackers during the process of distributing keys (Bennett & Brassard, 2020). PQC improves on existing algorithms to prevent network security threats from quantum computers by increasing the level of computational complexity.
Due to the influence of quantum computers, cases of networking with QKD have been studied worldwide. Typical examples of quantum cryptographic networks are Defense Advanced Research Projects Agency (DARPA) (2004) in the United States, Secure Communication based on Quantum Cryptography (SECOQC) (2008), Tokyo QKD (2010, 2013, 2015) in Japan, and the Beijing-Shanghai backbone quantum cryptographic network (2016). The DARPA Quantum Network (2002-2007) was the world’s first QKD network, operating ten optical nodes across Boston and Cambridge. The SECOQC network consists of a trusted private network and Quantum Back Bone (QBB). QBB provides quantum channel communication between QBBs and operates as a trusted private network, making it easy to register new end nodes in the QKD network. Tokyo QKD is a quantum cryptographic network configured using the Key Management System. Finally, China’s Beijing-Shanghai backbone quantum cryptography network combines ground and satellite links to form a total of 4,600 km of quantum cryptography communication networking.
Various studies have shown QKD to be safe from quantum computers; therefore, a variety of QKD protocols are being investigated (Sasaki, 2011).1 QKD can provide stable communication; however, it has many drawbacks with regard to network configuration. First, there are limitations on distance. Measurement-device-independent (MDI)-QKD is the QKD protocol with the longest distance of all QKD protocols that have been studied; it has a limit of 160-200 km. In addition, QKD is only capable of 1:1 communication because keys are distributed and divided between devices. Finally, construction costs are high because a quantum channel must be created for each device. Because of these drawbacks, it is impossible to create a national network using QKD.
The field of PQC is being studied to resolve the shortcomings of QKD, prevent security threats from quantum computing while using already-built networks, increase the computational complexity of existing algorithms, and develop new cryptography algorithms so that encrypted data cannot be decrypted by algorithms executed on quantum computers. However, PQC currently has the drawback of long encryption and decryption times because it increases computational and temporal complexity.
Therefore, in this study a network that combines QKD and PQC was designed and a network structure that utilizes the advantages of QKD and PQC is proposed. The network structure was configured using KREONET as a model, and there are plans to use it in the future. However, there are many limitations to designing a network that is safe from quantum computing using only QKD and PQC. In particular, because QKD performs only 1:1 communication and has a short communication distance, designing such a network incurs significant costs.
To overcome these drawbacks, we propose a QKD network structure that uses a quantum key management system (QKMS) and a Q-controller system. QKMS receives the symmetric key from a QKD and provides the key to the services that need encryption. During this process, QKMS creates a service key to efficiently use the symmetric key received from QKD, and the key lifecycle is managed to control these keys. In addition, QKMS overcomes the distance limitation by making it possible to relay keys. The Q-controller manages key relays and the QKMS.
2. QUANTUM KEY DISTRIBUTION AND POST QUANTUM CRYPTOGRAPHY
This section discusses QKD and PQC, which are needed to create a secure communication architecture using quantum cryptography. The network structure that is proposed in this paper provides a cryptography method for not only the backbone network, but also the user; therefore, it is necessary to improve the physical security of the backbone network that uses QKD and the security of the user terminal that uses the PQC.
QKD uses quantum properties to safely distribute symmetric keys between ‘Alice’ and ‘Bob.’ It has been extensively studied as a means of reliably distributing symmetric keys and is now the most actively researched area. The most typical QKD protocol is single photon-based BB84, which was developed in 1984 by Bennett and Brassard (Shor & Preskill, 2000). The BB84 protocol encodes information in the polarization of protons and transmits it through a quantum channel. Thereafter, the information is compared to obtain the same key. The polarization state of the proton changes due to measurement according to the principles of quantum mechanics; therefore, the error rate increases during the process of comparing information, and it is possible to determine the presence of an eavesdropper. In addition to this, QKD protocols are being studied in the form of various methods such as MDI-QKD and continuous-variable (CV)-QKD, along with satellite-based QKD systems. The following Table 1 summarizes the contents of various QKD protocols. Criteria for KREONET application were defined and each QKD protocol was analyzed.
Table 1
QKD protocol
| BB84 | E91 | SARG04 | DPS-QKD | COW-QKD | TF-QKD | MDI-QKD | CV-QKD | |
|---|---|---|---|---|---|---|---|---|
| Distance (km) | 70 | - | 90 | 260 | 125 | 550 | 390 | 140 |
| Star topology | Middle | Low | Low | Middle | Low | Low | High | High |
| Complexity | Middle | High | Middle | Middle | Middle | High | High | Low |
| Cost | Middle | High | High | Middle | Middle | High | High | Middle |
| Utilization | Low | Low | Low | Low | Low | Low | Low | High |
| Key rate | 3×10-7 | 5×10-7 | 1×10-5 | 1×10-38 | 9×10-5 | 2×10-6 | 5×10-6 | |
| Difficulty | Middle | High | Middle | Middle | Middle | High | High | High |
The QKD to be used in the Secure Communication Architecture proposed in this paper is not limited because it should be applied in various environments. However, there should be an interface and standard to obtain the key generated by QKD (ETSI, 2019, 2021; Länger & Lenhart, 2009). This is covered in detail in Section 3, QKMS.
PQC is being studied to resolve the shortcomings of QKD. It refers to a cryptography algorithm that can use existing network structures and cannot be decrypted by quantum computers. Because of these advantages, the National Institute of Standards and Technology (NIST) has been verifying various PQC algorithms, after a public call for standards in 2016 to standardize PQC. The types of PQC algorithms that are being studied include multivariate, code, grid, isogeny, and hash-based cryptography. Table 2 below shows the three round algorithms selected by NIST.
Table 2
PQC algorithms on 3 round NIST
| Finalists | Alternates | |
|---|---|---|
| KEMs/Encryption | Kyber | Bike |
| NTRU | FrodoKEM | |
| SABER | HQC | |
| Classic McEliece | NTRUprime | |
| SIKE | ||
| Signatures | Dilithium | GeMSS |
| Falcon | Picnic | |
| Rainbow | SPHINCS+ |
In the secure communication architecture proposed in this paper, the PQC algorithm is used in the user and institutional sections. The PQC algorithm is used among the algorithms selected in the third round of NIST. The reason for analyzing the selection of NIST before selecting the PQC algorithm is to apply it as a standard for the PQC algorithm in the future. Various services cannot be provided if a non-standard PQC algorithm is used in a quantum cryptographic communication network that will provide various vendors and services. Therefore, in this paper we will apply TLS v1.3, which can apply the PQC algorithm, and then apply the PQC algorithm in future work. In addition, the PQC algorithm is applied to TLS v1.3 and used for sections where QKD cannot be installed.
Therefore, to design a cryptographic communication structure that uses quantum cryptography, research must be conducted on not only QKD but also PQC applications. In this paper, we propose a method that uses QKD to set up completely safe intervals and the PQC algorithm to decrease costs and increase network users in the future.
3. QUANTUM KEY MANAGEMENT SYSTEM
This section discusses the QKMS in detail. The QKMS receives symmetric keys from the QKD, generates service keys for an efficient key usage rate, and provides keys that are suitable for service security requirements. In addition, the QKMS performs key relay functions to allow long-distance QKD communication and performs key management to provide a stable cryptography service. Table 3 lists the required functions of the QKMS.
Table 3
Function of QKMS
As shown in Fig. 1, the QKMS is an essential component for creating a network with QKD. The structure of the QKMS was designed as shown in Fig. 1 to perform the required functions listed in Table 1. The essential components of QKMS are Key Management Agent (KMA), Key Supply Agent (KSA), and Key Relay Agent (KRA). The KMA is a module that receives symmetric keys from the QKD and reformats the keys for efficient key usage. In addition, it is necessary to perform functions such as ensuring storage space using key life cycle management and reducing the error rate when synchronizing keys. To reliably perform the functions, the QKD protocol abstraction layer must perform an adapter role to receive keys that are generated by the various types of QKD, so that the Quantum Key Distribution Entity (QKDE) manager module can receive information related to QKD and maintain a stable network. A key receiving protocol based on the ETSI QKD 014 standard must be configured to allow the adapter to receive stable keys. The KSA is a module that provides keys suitable for service security requirements. To provide these keys, the KSA must be designed to support various services through an network entity (NE) protocol abstraction layer, and to perform all tasks related to the service keys. Finally, the KRA is a module that relays keys for long-distance quantum cryptography communication. To efficiently relay keys, the KRA must use the QKMS manager to check the state of the components and the topology and set up of key relay routes.
Fig. 1
QKMS structure. QKMS, quantum key management system; QKDE, quantum key distribution entity; KMA, key management agent; KSA, key supply agent; KRA, key relay agent; RNG, random number generator; OTP, one time password; NE, network entity; PoTN, packet optical transport network.
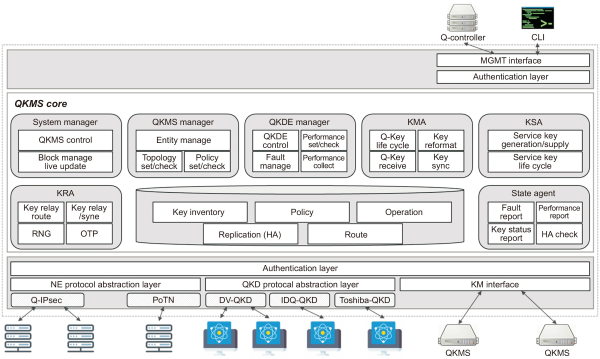
Fig. 1 shows that the QKMS requires various modules in addition to KMA, KRA, and KSA. QKMS has a 1:N structure that can be linked to multiple QKDs; therefore, it must be able to distinguish keys generated by each linked QKD, and the messages for sending and receiving keys must be in the same format. Therefore, the messages sent by heterogeneous QKD devices are converted to the ETSI QKD 014 standard format in the QKD protocol abstraction layer, and the keys are sent to the KMA. The system manager controls the QKMS itself and manages each of the modules. Finally, the state agent ascertains the states of the QKMS-linked QKD, the QKMS, and the channels, as well as monitoring their performance and key states. In addition, the QKMS-QKD section is defined as a security setting zone, and the QKMS-User section can be safely key transferred by applying the PQC algorithm.
4. Q-CONTROLLER
The Q-controller performs the overall management of a quantum cryptography communication network that consists of QKMS and QKD, and is responsible not only for managing the quantum keys generated by QKD within the quantum cryptography communication network, but also for managing the service keys generated by QKMS. It also manages the component devices and channel states that make up the quantum cryptography communication network. In addition, The Q-controller monitors the performance of each device to create a seamless quantum cryptography communication network, handles disruptions that occur while managing the devices, and provides notifications about them. Table 4 lists the required functions of the Q-Controller.
Table 4
Function of Q-controller
The Q-controller, which performs the functions in Table 4, is a device that allows for centralized management when creating a quantum cryptography communication network. It is composed of four modules, as shown in Fig. 2. The quantum key distribution network (QKDN) manager module manages its component devices and provides a live update function that allows state information to be checked in real time. It also performs functions that allow disruptions, performance, and key states to be checked when examining state information. In addition, it can set policies in the key management network, and check the current state of the network. The topology manager checks and manages the quantum cryptography communication network’s topology state to allow for efficient key relaying by determining optimal routes when relaying keys within the QKMS. To efficiently perform the key relay function, the key relay manager checks and manages the key generation states from QKMS, searches and generates relay routes, and generates alternate routes to handle relay route disruptions. Finally, the state manager receives notifications regarding disruptions, handles these disruptions when they occur in the components of the quantum cryptography communication network, and receives key state and performance information.
Fig. 2
Q-controller structure. GUI: graphical user interface; QKMS, quantum key management system; QKDN, quantum key distribution network.
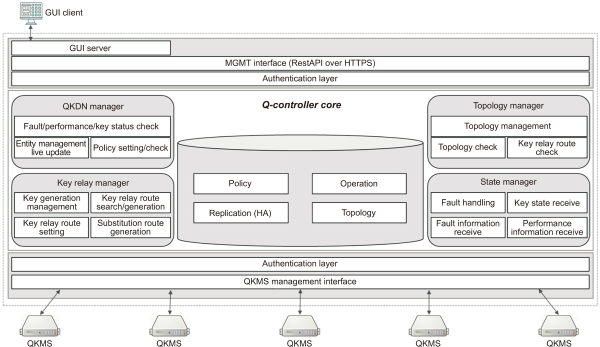
The Q-controller consists of an authentication layer, interface, and a graphical user interface (GUI) server in addition to the four main modules. Because the Q-controller is linked to the QKMS and users, only the authenticated QKMS and users should have access; the authentication layer checks this process. A GUI client is used to allow the administrator to easily access the Q-controller, and the GUI server allows the Q-controller to be operated by sending and receiving messages.
5. SECURE COMMUNICATION ARCHITECTURE APPLYING QUANTUM CRYPTOGRAPHY
This section proposes a cryptographic communication structure that consists of the aforementioned QKD, PQC, QKMS, and Q-controller. The structure was designed based on a science and technology research network (Kim et al., 2018; KREONET, 2021; Park et al., 2010). In this network, a backbone section was designed focusing on 17 regional network centers in Korea. Because each regional network connects to all users, it is necessary to create a design that improves the security of the connections between users to build a quantum cryptography communication network based on the science and technology research network. Therefore, a network structure that consists of the QKD, PQC, QKMS, and Q-controller was designed to build a quantum cryptography communication network based on the science and technology research network.
Fig. 3 shows the design of the national research network-based quantum cryptography communication network. The backbone sections and the sections between the backbone and the organizations are designed with the QKD, which is expensive but stable. The sections between the organizations and the users are designed with PQC, which has a lower stability and design cost than QKD and is able to use the existing network. The QKMS was included to efficiently link the QKD and PQC and manage the keys that are distributed by the QKD. The Q-controller was included to organize the overall quantum cryptography communication network.
Fig. 3
Secure communication architecture applying quantum cryptography. QKD, quantum key distribution; QKMS, quantum key management system.
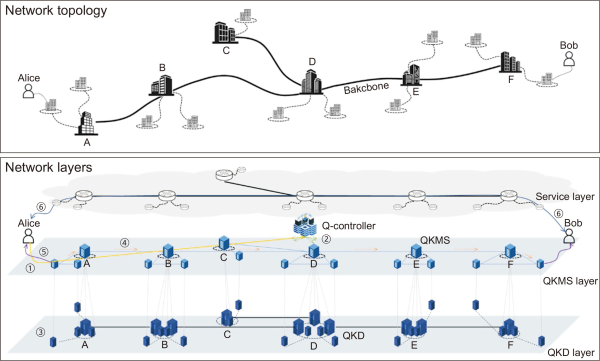
If the quantum cryptography communication network is implemented as in Fig. 3, a centralized administrator can manage the network via the Q-controller, and quantum cryptography communication can be set up. The Q-controller receives the QKD, QKMS, and channel state information via each QKMS, and can manage disruptions in components. In addition, the Q-controller calculates efficient key relay routes, and relays commands to each QKMS to make long-distance communication possible.
For Alice and Bob to perform quantum cryptography communication as shown in the figure, the following procedure is carried out. 1) Alice sends a quantum cryptography communication request to a nearby QKMS, and the QKMS relays the request to the Q-controller. 2) The Q-controller checks the recipient of the message, calculates the route, and relays key request messages to each QKMS on the route. 3) The QKMSs that have received requests send generation request messages to the QKD, and the QKD generates the keys. 4) The keys are relayed along the route by the Q-controller, and the QKMS near Alice and Bob share symmetric keys. 5) The QKMSs perform encryption via the PQC and relay the symmetric keys to Alice and Bob. 6) Alice and Bob communicate by encrypting data using the shared symmetric keys.
6. SIMULATION
This section deals with the results of verifying the proposed quantum cryptographic network design. The simulation environment consists of one Q-controller and three QKMS nodes as shown in Fig. 4. QKD is replaced by a simulator because it is currently in the development stage (Ma et al., 2016). The verification scenario is carried out in the following Table 5.
Fig. 4
Simulation environment. SAE, security application entity; QKD, quantum key distribution; QKMS, quantum key management system.
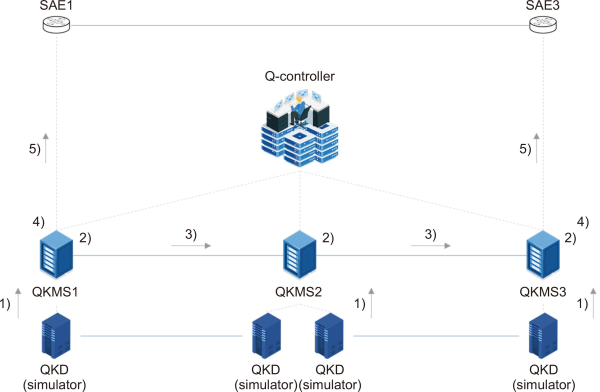
Table 5
Verification scenario
| Step | Content | Verification function |
|---|---|---|
| 1 | Key generated by QKD simulator received from QKMS (QKMS1-2, QKMS2-3) | The function of key receives |
| 2 | QKMS reformat the received key (QKMS1-2, QKMS2-3) | The function of key reformats |
| 3 | Key relay via QKMS2 | The function of key relay |
| 4 | Synchronize keys on QKMS1, 3 | The function of key synchronizes |
| 5 | Service key provided by QKMS1, 3 | The function of key supplied |
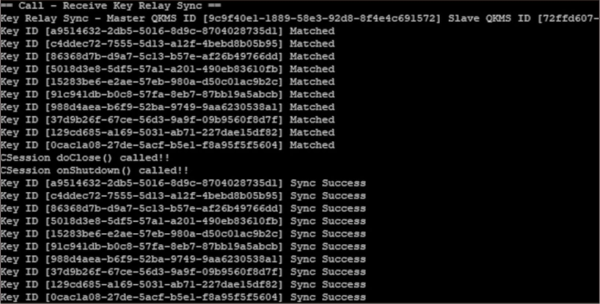
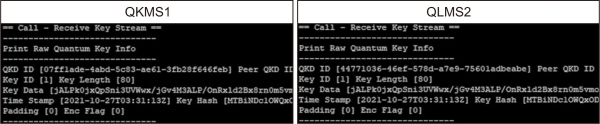
The verification results are checked for each verification stage as follows. First, Fig. 5 confirms the key generated by the QKD simulator in QKMS1 and 2. It was confirmed that QKMS1 and QKMS2 have the same symmetric key.
Fig. 5
Key generated by QKD simulator in QKMS1 and QKMS2. QKD, quantum key distribution; QKMS, quantum key management system.
The next step is the function of the QKMS to reformat the received key for efficient use (Krawczyk & Eronen, 2010). The reformat function confirms that 10 keys with 8 length are generated with 80 length keys, and using the reformatted keys, QKMS1 relays to QKMS3 through QKMS2. After completing the relay, the QKMS1 and the QKMS3 synchronize and match each other’s keys to check the relay result. The Fig. 6 shows a state in which QKMS1 and QKMS3 have the same key as each other through a key relay.
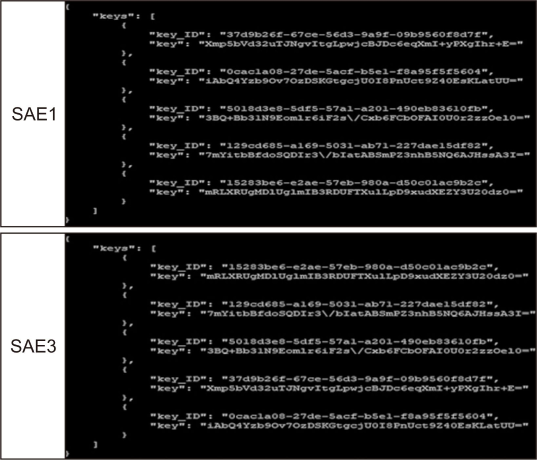
Finally, it is confirmed that the symmetric keys of QKMS1 and QKMS3 are supplied to perform the role of QKMS. The Fig. 7 is the result of SAE1 and 3 confirming the supply to the security application entity (SAE) connected to QKMS1, 3. It was confirmed that the two SAEs received a symmetric key.
7. CONCLUSION
This paper proposes a quantum cryptography communication network that consists of a QKD and PQC. The QKMS was used to overcome the disadvantages of QKD, including the 1:1 communication and distance limitations, and a stable quantum cryptography communication network was constructed by substituting PQC for QKD at the user end, as QKD cannot be installed at the user end and incurs a high cost. The proposed quantum cryptography communication network uses the QKMS to incorporate networking into the QKD and to relay keys using PQC. The functions of the QKMS were defined and designed to manage the QKMSs that make up the quantum cryptography communication network and set efficient key relay routes. The processes that constitute quantum cryptography communication between users via the designed items were shown for each layer, and a stable quantum encrypted communication method was proposed. In future studies, the QKD that is currently implemented in the simulator will be converted into an actual QKD and linked to the QKMS, and an actual quantum cryptography communication network will be applied to a national science and technology research network.
1 See also: Chen et al., 2009; Elliott et al., 2003; Elliott & Yeh, 2007; European Commission, 2017; Han et al., 2010; Langer, 2013; Peev et al., 2009; Qiu, 2014; Sergienko, 2005; Shimizu et al., 2014; Travagnin & Lewis, 2019; Wang et al., 2014; Wang et al., 2010; Wu et al., 2009; Zhang, 2017; Zhang et al., 2018; Zhao, 2019.
REFERENCES
, (2007) DARPA quantum network testbed Defense Technical Information Center https://books.google.co.kr/books/about/DARPA_Quantum_Network_Testbed.html?id=W_IpnQAACAAJ&redir_esc=y
ETSI (2019) Quantum key distribution (QKD); Protocol and data format of key delivery API to applications, GS QKD 014, V1.1.1 https://www.etsi.org/deliver/etsi_gs/QKD/001_099/014/01.01.01_60/gs_qkd014v010101p.pdf
ETSI (2021) Quantum key distribution (QKD); Control interface for software defined networks, GS QKD 015 V1.1.1 https://www.etsi.org/deliver/etsi_gs/QKD/001_099/015/01.01.01_60/gs_QKD015v010101p.pdf
European Commission (2017) China to launch world's first quantum communication network https://cordis.europa.eu/article/id/122516-trending-science-china-to-launch-worlds-first-quantum-communication-network
, , , , , , , , , , (2010, March 21-25) An application-oriented hierarchical quantum cryptography network test bed Proceedings of the 2010 Conference on Optical Fiber Communication (OFC/NFOEC), Collocated National Fiber Optic Engineers Conference IEEE An application-oriented hierarchical quantum cryptography network test bed, 1-3,
, , , (2018) KREONET-S: Software-defined wide area network design and deployment on KREONET IAENG International Journal of Computer Science, 45(1), 27-33 https://scholar.google.co.kr/citations?view_op=view_citation&hl=ko&user=BP4sjXsAAAAJ&citation_for_view=BP4sjXsAAAAJ:u5HHmVD_uO8C.
, (2010) HMAC-based extract-and-expand key derivation function (HKDF) https://www.hjp.at/doc/rfc/rfc5869.html
KREONET (2021) KREONET web site http://www.kreonet.net/
, (2009) Standardization of quantum key distribution and the ETSI standardization initiative ISG-QKD New Journal of Physics, 11(5), 055051 https://iopscience.iop.org/article/10.1088/1367-2630/11/5/055051.
, , , (2010) A study of future internet testbed construction using NetFGA/OpenFlow switch on KOREN/KREONET Journal of the Institute of Electronics Engineers of Korea TC, 47(7), 109-117 https://www.koreascience.or.kr/article/JAKO201030853094488.j.
, , , , , , , , , , , , , , , , , , , (2009) The SECOQC quantum key distribution network in Vienna New Journal of Physics, 11, 075001 https://iopscience.iop.org/article/10.1088/1367-2630/11/7/075001.
(2017) Quantum tech to link Jinan governments https://global.chinadaily.com.cn/a/201707/11/WS59bbe9fca310ded8ac18c53a.html
- Submission Date
- 2022-04-20
- Revised Date
- 2022-05-09
- Accepted Date
- 2022-05-17
- Downloaded
- Viewed
- 0KCI Citations
- 0WOS Citations