Breaking the Code of Silence: A Qualitative Exploration of Cyberbullying Through the Lens of Habermas’s Theory of Communicative Action

Joshua Isaguirre (College of Engineering, Architecture and Technology, De La Salle University-Dasmariñas, Cavite, Philippines)

Elanie Vizconde (Technological University of the Philippines, Manila, Philippines)

Raymund Sison (College of Computer Studies, De La Salle University, Manila, Philippines)
Abstract
This qualitative study explores cyberbullying among college students through Habermas’s Theory of Communicative Action to examine the dissonance between online interactions and principles of rational discourse. Cyberbullying is a pervasive issue in digital communication that undermines logical, evidence-based conversation, fostering environments where misinformation, manipulation, and harm thrive. By analyzing case studies from three universities, the research identifies the characteristics, dynamics, and emotional impacts of cyberbullying on victims, highlighting the role of social media platforms in facilitating these negative interactions. The findings reveal significant challenges to authentic and equal online conversations, driven by power imbalances and a lack of genuine communication, leading to psychological distress, erosion of self-esteem, and changes in behavior among victims. The study underscores the potential of social media design and policy interventions to mitigate cyberbullying, emphasizing the need for educational programs, technological solutions, and community support to promote a safer, more respectful digital environment. Key themes include the dynamics of cyberbullying, the suppression of rational discourse, the psychological and emotional consequences of inauthentic communication, and strategies for resilience and recovery. The research contributes to understanding cyberbullying’s complexities and suggests a multifaceted approach to addressing it, aligning with Habermas’s ideal of communicative rationality to foster healthier online communities. Future research should further explore the intersection of technology design, user behavior, and regulatory policies to combat cyberbullying effectively.
- keywords
- cyberbullying, rational discourse, social media bullying, Theory of Communicative Action
1. INTRODUCTION
In today’s world, where digital communication connects us all, a new challenge emerges: The tools that help us stay connected can also introduce new threats. Cyberbullying is a serious concern in this digital era, breaking free from the constraints of location and time. This issue has evolved from traditional bullying and is taking a new shape with the rise of digital technologies (Della Cioppa et al., 2015; Suler, 2004; Vismara et al., 2022).
The dual nature of social media as both a primary source of information and misinformation highlights its significant role in shaping public perceptions and interactions (Catedrilla et al., 2020; Ebardo et al., 2020; Ebardo & Suarez, 2023). With the rise of Internet use and the popularity of social media, people increasingly turn to platforms like X (formerly Twitter) and Facebook. However, this shift brings challenges, such as the risk of exposure to inaccurate information. Further, digital technologies have made it easier for people to engage in harmful behaviors online, with less restraint than in in-person interactions (Suler, 2004). Social media platforms are now battlegrounds for cyberbullying, affecting a significant portion of teenagers worldwide and raising concerns among parents and educators (Badri et al., 2017; Choi et al., 2021; Conde, 2022; Eweida et al., 2021; Farrington et al., 2023; Ortiz-Ospina, 2019; Patchin & Hinduja, 2006; Ramos Salazar, 2021; Saleem et al., 2022; Xu & Trzaskawka, 2021). Cyberbullying manifests in various forms, including threats, unauthorized sharing, impersonation, and spreading rumors (Erbiçer et al., 2023; Patchin & Hinduja, 2006; Willard, 2007), leading to negative impacts on young people’s self-esteem, emotional well-being, and behavior, sometimes even resulting in suicidal thoughts (Chen et al., 2017; Erbiçer et al., 2023; Garett et al., 2016; Hinduja & Patchin, 2010). There is a noticeable gap in research on cyberbullying among college students, especially in the Philippines (Cocal, 2019; Costales et al., 2022).
This study investigates cyberbullying through the lens of Habermas (1984)’s Theory of Communicative Action. Our goal is to determine whether online interactions follow or stray from the principles of rational discourse. By ‘rational discourse,’ we mean discussions where logic, evidence, and reasoning guide conversations toward informed conclusions rather than being driven by emotions or biases. We aim to understand how online platforms either discourage or enable cyberbullying, focusing on the role of IT design and policy in fostering a safe and genuine digital communication space. In the next section, we explore Habermas (1984)’s Theory of Communicative Action, providing a theoretical basis for our study. Section 3 covers our research methods. Section 4 shares our findings. Section 5 concludes the paper, discussing the implications and limitations of our study and suggesting directions for future research.
2. HABERMAS’S THEORY OF COMMUNICATIVE ACTION
This section explores the impact of cyberbullying on social media among college students through the lens of Habermas (1984)’s Theory of Communicative Action. Habermas’s theory, emphasizing the importance of rational, open discussion, is an excellent framework for analyzing how cyberbullying disrupts effective digital communication. At the core of Habermas’s approach is the idea of ‘communicative rationality,’ a form of debate free from domination, where the merit of arguments is evaluated based on their quality and relevance (Cecez-Kecmanovic, 1995). According to this theory, communication, mainly through language, is a tool for individuals to achieve mutual understanding and coordinate actions that reflect collectively agreed-upon meanings. This approach is crucial for the health of a democratic society, fostering a culture where discourse is aimed at understanding rather than winning (Baxter, 2011).
Habermas distinguishes between two types of actions within communication: communicative action and strategic behavior. Communicative action is about engaging in dialogue with the intent of mutual understanding, where words convey meanings and achieve common goals. Strategic behavior, conversely, aims to elicit specific reactions from others, often disregarding the pursuit of mutual understanding (Habermas, 1984). The essence of Habermas’s theory is this distinction, advocating for authentic communication aimed at understanding and respecting different viewpoints, meeting criteria of clarity, truthfulness, and shared expectations (Habermas, 1984; Ross & Chiasson, 2011). This study employs Habermas’s concepts to investigate the extent to which cyberbullying undermines the envisioned ideal situation of communication.
As proposed by Habermas (1984, p. 255-256), the four principles of rational discourse have been effectively summarized by Klein and Huynh (2004).
-
1) Opportunity for Speech Acts: Getting a chance to talk or communicate. All participants should have the same opportunities to initiate and sustain a conversation, engaging in dialogues and making statements and rebuttals.
-
2) Interpretation and Validation: Understanding what is being said and evaluating its truth or integrity. Participants should have the same opportunities to interpret, assert, recommend, explain, justify, question, or provide evidence supporting or opposing any claim. This ensures that every opinion or presupposition can eventually become the focus of discussion and scrutiny.
-
3) Honest Expression: Being genuine and sincere when communicating. All participants should be equally capable of expressing their attitudes, feelings, and intentions, safeguarding against self-deception, illusions, and insincerity within the community.
-
4) Regulative Speech Acts: These are the guidelines for our spoken and nonverbal conduct during communication. Participants should be equally able to provide and deny permissions, make and request promises, account for actions, and demand explanations, ensuring equal opportunity for discourse initiation and continuation.
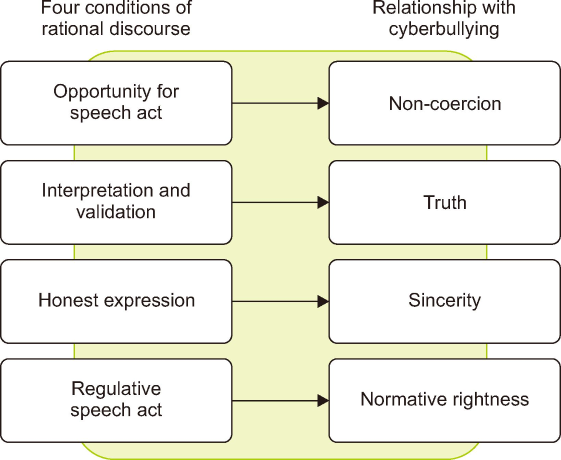
Applying the four conditions of the rational discourse theory to cyberbullying, we can analyze the implications for addressing this issue. Fig. 1 below shows the relationship between how the rational discourse theory by Habermas can explain cyberbullying incidents.
-
1) Non-coercion: In a fair conversation, everyone should be free to speak their mind without feeling pressured or forced by others. Everyone’s opinion is valued and respected equally.
-
2) Truth: In a reasonable discussion, what people say should be factual and evidence-supported. The interchange should be about being honest and not making things up. The notion of truth revolves around practicing honesty and refraining from fabricating information.
-
3) Sincerity: This involves communicating with sincerity and expressing oneself authentically without any intention to deceive or mislead others. In cyberbullying, sincerity pertains to the genuine expression of beliefs and intentions by the individuals involved.
-
4) Normative Rightness: This ensures that the arguments presented in a conversation conform to widely recognized principles and ethics.
3. METHODOLOGY
This section describes the qualitative interpretive methodology underpinning our multiple case study, as Yin (2009) recommended. The methodology enabled a thorough investigation of cyberbullying encounters among university students on social media platforms.
3.1. Research Design
Utilizing an explanatory multi-case approach, our study used Habermas (1984)’s Theory of Communicative Action principles and qualitative research to investigate the phenomena within its real-life setting (Yin, 2009). This design was selected based on examining intricate social phenomena and comprehending the subtle experiences of individuals in their natural settings (Denzin & Lincoln, 2011).
3.2. Case Selection
Following Yin (2009)’s recommendations, we conducted a detailed examination of eight cases conveniently selected from three universities (for ethical reasons, we named them Universities X, Y, and Z). The selection criteria were designed to ensure a rich diversity of experiences, aiming for depth over breadth (Creswell, 2007; Stake, 2006). According to Creswell and Creswell (2018), no specific minimum number of participants is needed for qualitative interviews. This is because qualitative research prioritizes the depth and richness of data rather than quantifiable validity indicators. For case study design, the Creswell and Creswell (2018) suggest that even a single case can be profoundly informative if it is well-chosen, critical, unique, or revealing. That will best help to understand, explore, and explain the phenomenon of interest.
Participants were selected through a purposive sampling method, targeting individuals from universities X, Y, and Z (which have been anonymized for confidentiality purposes) who have experienced cyberbullying. This selection aimed to capture diverse cyberbullying experiences by including participants from varied university settings. Our methodological approach was designed to yield in-depth insights into the multifaceted nature of cyberbullying across different educational environments. To ensure the inclusion of individuals who genuinely encountered cyberbullying, we relied on self-reported experiences confirmed through initial screening processes:
-
Individuals who reported experiencing cyberbullying events at least once a month over the past six months, ensuring recent and potentially ongoing exposure to cyberbullying.
-
Individuals encountering various forms of cyberbullying, such as online harassment, cyberstalking, or denigration.
-
Participants who expressed a readiness to discuss their experiences in detail, whether through in-depth or in-person interviews. This willingness was crucial for gathering rich, qualitative data on the personal impacts of cyberbullying.
Initial identification of potential participants was conducted via online surveys distributed through university email lists. The surveys also served as a preliminary screening tool to assess the frequency and types of cyberbullying experiences among respondents. Following this, students who met our criteria based on their survey responses were contacted for further evaluation through an initial brief interview via email or phone, where we clarified their experiences and ensured their willingness to participate in more extended, semi-structured interviews.
After agreeing to participate, participants received invitation and consent forms, which detailed the study’s purpose, procedures, and ethical considerations. These forms also emphasized their rights as participants, including the right to withdraw from the study at any point without repercussion and the option to request the removal of any of their statements from the research findings.
3.3. Data Collection
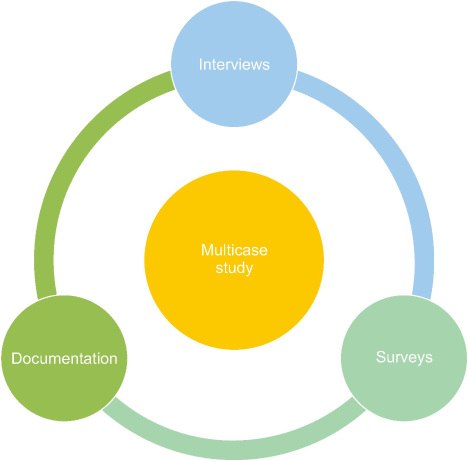
This study collected data using interviews, surveys, and documentation (Fig. 2). The study’s validity is strengthened through data triangulation (Yin, 2017).
Semi-structured interviews allowed participants to express their cyberbullying experiences in depth. The data collecting method of choice was semi-structured online interviews conducted through platforms via Google Meet or Zoom for convenience. Follow-up inquiries were conducted via chat or email. The researcher prioritized the anonymity and privacy of the participants by employing pseudonyms to safeguard their identities. The interviews were recorded solely for data collection and were securely saved with password protection. The interview questions encompass a range of subjects about cyberbullying encounters, emotional effects, coping mechanisms, societal norms, and the influence of peers. Furthermore, using a semi-structured framework facilitated the process of probing and clarification, leading to a deeper understanding of the phenomena being investigated. Throughout the interview, participants were allowed to express any additional knowledge or concerns not covered by the questions. To enhance the reliability of the data, the researcher implemented member checking, a method wherein the participants were given access to their interview transcripts to validate the precision of the recorded data and the conclusions drawn from the study (Creswell, 2007). This methodology improves the veracity and reliability of the study.
Document analysis involves systematically collecting and examining diverse textual data derived from social media platforms such as Facebook. This includes scrutinizing social media posts, messages exchanged through messenger services, and user comments. The study of documentation entailed scrutinizing the language and context of cyberbullying interactions on Facebook, which was found to be the most prominent venue for such activities within our sample.
Qualitative research involves using surveys to identify and examine the variety within a particular population. However, the primary aim of this study is not to ascertain frequencies, means, and other statistical measures, but rather to evaluate the level of diversity related to a particular subject of interest within a given population (Jansen, 2010). Google Forms was used to conduct the survey. This method was chosen for its convenience and easy accessibility through email, making it suitable for efficiently reaching many respondents. Moreover, this approach required minimal time and cost for both the researchers and participants. The estimated completion time for the survey was less than 10 minutes. The survey questionnaire was distributed conveniently among students from three participating universities involved in the study.
3.4. Database Management
A case study database was established to organize and manage the data systematically, in alignment with Yin (2017)’s guidelines. This facilitated an efficient analysis process and ensured the traceability of conclusions back to the original data. For example, interview transcripts were called ‘Transcript_Case1,’ ‘Transcript_Case2,’ etc. This standardized naming approach made data administration easy.
3.5. Data Analysis of the Multiple Case Study
The analysis was conducted using a three-phase methodology, following Yin (2017)’s methodological structure. At first, a within-case analysis was conducted to emphasize the distinctive characteristics of each instance, focusing on their individuality. The researchers categorized the initial classifications into the main themes using categorical aggregation. Stake (2006) defines categorical aggregation as combining category data by addition. In this section, the themes identified through the analysis of the case studies are given. The relevance of the findings can be inferred from the themes identified. Subsequently, a cross-case analysis was conducted to identify repeating patterns and variations across the different cases, providing a comparative viewpoint. Then, the process of assertion analysis was employed to incorporate the data into the existing theoretical framework, making it easier to evaluate the main themes and derive implications from the study. The analysis of statements or the interpretation of cases constitutes the concluding phase of analysis in a multi-case study (Creswell, 2007; Merriam, 2009). Table 1 shows sample coding, and Table 2 the derived theme.
Table 1
Sample coding
| Sample incident | Code | Concept |
|---|---|---|
| “Your personality belongs to the trash.” (1.13) | Insult, degrade | Speech acts in cyberbullying |
| “They kept posting ‘#Aling Bebang problems.’” (1.2) | Public humiliation, indirect insults | Speech acts in cyberbullying |
| “The third time was when my friends made a group chat in Messenger without me.” (1.14) | Secretive backstabbing | Role of social media, power dynamics |
| “They made it as a medium for backstabbing.” (1.15) | Social exclusion | Role of social media, power dynamics |
| “Peer influence did play a role as my cyberbullies took advantage of their spheres of influence in order to conform my other classmates to say bad things about me as well.” (1.89) | Peer pressure and groupthink | Role of social media, power dynamics |
Table 2
Emergence of themes
3.6. Ensuring Research Quality
We addressed construct, external, and internal validity through methodological rigor, participant diversity, and member checking, per Yin (2017)’s criteria for multi-case study research.
3.7. Ethical Considerations
The research was conducted strictly in compliance with the ethical standards outlined in the Research Service Agreement (F-URD-4.1-RSA, dated 11/19/2019). Before their participation, all individuals were thoroughly briefed on the study’s objectives, assured of the confidentiality of their responses, and informed of their right to withdraw from the study at any time without any repercussions. Written informed consent was obtained from every participant, affirming their voluntary engagement and comprehensive understanding of the study’s procedures. To safeguard the participants’ anonymity and the sensitive nature of the information collected, extensive measures were implemented to anonymize and securely store data, consistent with the guidelines and ethical standards of the university.
4. RESULTS
An overview is provided for each student affected by cyberbullying, with pseudonyms ensuring their anonymity, as shown in Table 3.
Table 3
Participants’ profiles
| Case No. | Pseudonym | Sexual orientation |
|---|---|---|
| 1 | Bebang | Female |
| 2 | Alexis | Female |
| 3 | Johnny | Gay |
| 4 | Trixy | Female |
| 5 | Brent | Male |
| 6 | Andrew | Male |
| 7 | Rasheed | Male |
| 8 | Marcus | Male |
4.1. Case Study Overview
The study involves participants from various academic backgrounds, assigned pseudonyms for privacy. It includes four students from public University X enrolled in chemistry, elementary education – language, and information technology. Additionally, two participants studied computer engineering at the private University Y, while another two pursued computer science and computer engineering at the public University Z. This mix of public and private urban university participants enriches the study with varied experiences and perspectives.
4.1.1. Case Study 1: Bebang
Bebang is known for her energetic and straightforward nature. She consistently demonstrates enthusiasm when sharing her perspectives, viewpoints, and personal anecdotes on diverse social media platforms, including Facebook, Instagram, and X. She believes that her regular social media engagement has facilitated the development of more profound connections with her peers. Sadly, Bebang’s open and honest nature has made her vulnerable to cyberbullying, which includes being publicly mocked through hashtags and being targeted in a secret group chat aimed at undermining her.
4.1.2. Case Study 2: Alexis
Alexis, who loves joining school contests, was taken aback when friends turned against her online. Using a secret photo, her friends made mean edits to make her look bad, uttering derogatory remarks on Facebook due to her academic success. This betrayal made her feel alone and misunderstood, thinking all her friendships were fake. Since then, she has become much more private, sharing less online and discreetly monitoring the activities of her former friends.
4.1.3. Case Study 3: Johnny
Johnny was first bullied online through name-calling. He felt betrayed by friends who secretly mocked him in a group chat, not knowing why. Struggling with depression and self-harm, he wore jackets on sunny days to hide his scars. His peers then ridiculed him on Facebook, claiming he sought attention. This breach of trust from a friend he confided in about his depression, who shared his struggles in the group to mock him.
4.1.4. Case Study 4: Trixy
Trixy was once on her way to becoming a popular influencer but had to stop because of cyberbullying. She faced not just name-calling and harsh criticism but also sexual harassment, shockingly from someone she knew. This harassment spread across several platforms, including TikTok, Instagram, X, Facebook, and Messenger, impacting her profoundly and forcing her to reconsider her online presence.
4.1.5. Case Study 5: Brent
Brent is highly esteemed by both his peers and academics due to his exceptional academic achievements and active involvement in extracurricular activities, which serve as evidence of his abilities and competitive nature. A disagreement related to a thesis project resulted in the proliferation of adverse sentiments directed toward him in this online space.
4.1.6. Case Study 6: Andrew
Andrew can be defined as tall, dark, and handsome. From how he dresses, conducts himself towards others, and his manners, one can understand that he is humble and good. However, it can be noticed that Andrew has many insecurities and exhibits traits of anxiety. His self-esteem was destroyed by insulting language and harsh criticisms from individuals he relied on in social media, which created a toxic environment. The cyberbullying he experiences, especially from those he values, dramatically affects his outlook on life.
4.1.7. Case Study 7: Rasheed
Although Rasheed values his privacy on social media, his academic accomplishments have unfortunately made him a subject of cyberbullying across multiple platforms. The bullying originated from unfounded allegations made by his colleagues, who suspected that Rasheed leveraged his connections with his homosexual professor to obtain high academic scores. Motivated maybe by envy, certain peers subjected him to ridicule based on an inferred sexual orientation, both face-to-face and via malicious Facebook postings and comments.
4.1.8. Case Study 8: Marcus
Marcus is a passionate gamer. He joined a Facebook group to establish connections with like-minded gaming enthusiasts. However, he encountered cyberbullying when his viewpoints conflicted with those of other members of the community. As a result of this incident, he has been more cautious and conservative regarding revealing personal information online and is now more skeptical of trusting strangers on social media platforms.
Analyzing these eight cases within the framework of Habermas’s principles reveals how cyberbullying infringes upon the ideals of communicative action, specifically regarding Equal Opportunity for Speech Acts, Truth, Sincerity, and Normative Rightness (Table 4 reflects the impact of cyberbullying on adherence to Habermas’s principles across different cases).
Table 4
Analysis of the case within the framework of Habermas’s principles
| Case | Equal opportunity for speech acts | Truth (validity claims) | Sincerity (truthfulness) | Normative rightness (legitimacy) |
|---|---|---|---|---|
| 1: Bebang | Suppressed by public mockery and secret groups, limiting free expression | Distortion through mockery challenges truthfulness | Anonymity used for insincere attacks | Mockery undermines ethical standards of respect |
| 2: Alexis | Became more private, reducing participation due to cyberbullying | False narratives created through derogatory remarks | Betrayal reflects a lack of sincerity | Violation of dignity through betrayal and manipulation |
| 3: Johnny | Silenced by ridicule, hindering willingness to engage | Misuse of personal information distorts truth | Breach of trust indicates insincerity | Mocking mental health struggles violates ethical interaction norms |
| 4: Trixy | Overwhelmed by harassment, forced to reconsider online presence | Unfounded claims and insults distort truth | Sexual harassment from a known person signifies deep insincerity | Harassment severely breaches norms of respectful communication |
| 5: Brent | Adverse sentiments limit ability to communicate freely | Rumors likely contain distortions challenging reputation | Spreading of rumors reflects departure from sincerity | Targeting undermines the legitimacy of academic discourse |
| 6: Andrew | Insulting language and criticism restrict participation and self-expression | Personal insecurities exploited, likely involving false narratives | Deceitful bullying exploits vulnerabilities, lacking sincerity | Toxic environment created by bullying violates ethical communication |
| 7: Rasheed | Restricted ability to defend integrity, limiting open engagement | Baseless allegations challenge the truth of academic merit | Personal attacks undermine sincerity of community interaction | Bullying based on unfounded allegations breaches ethical norms |
| 8: Marcus | Skepticism and withdrawal limit engagement in gaming community | Conflict distorts viewpoints, affecting truthfulness | Personal attacks escalate disagreements, lacking sincerity | Community’s failure to maintain respect questions normative rightness |
Principle 1. Equal Opportunity for Speech Acts (Universal Access): Every participant in a discourse must have an equal opportunity to initiate and continue communication. This includes the right to question, introduce assertions, express attitudes, desires, and needs, and explain or justify these expressions. This principle is essential for ensuring that all voices can be heard and considered equally, which is fundamental to achieving genuine understanding and consensus.
Principle 2. Truth (Validity Claims): Discrete statements are expected to be truthful, and participants must agree on the truth of the propositions discussed. This implies that participants have the shared goal of reaching an understanding based on facts and shared experiences, allowing for a common ground of reality to be established and validated through discourse.
Principle 3. Sincerity (Truthfulness): Participants must mean what they say, with expressions reflecting their actual intentions and beliefs. This honesty is crucial for building trust within the discourse, as it ensures that participants are not attempting to deceive each other and are genuinely striving for mutual understanding.
Principle 4. Normative Rightness (Legitimacy): The contributions of each participant must be appropriate and conform to the recognized norms of the discourse community. This principle ensures that interactions are governed by a shared understanding of what is considered right and acceptable within the context of the discourse, supporting an environment of respect and ethical communication.
In the following:
4.1.8.1. Case Study 1: Bebang.
Bebang’s experience shows a clear violation as cyberbullying restricted her from freely expressing herself on social media, a platform meant for open communication. The public mockery and secret chats likely propagated falsehoods or exaggerations about her, distorting the truth of her character and actions. The anonymity and secrecy of the cyberbullying acts call into question the sincerity of the communication, allowing perpetrators to hide behind digital facades. The ethical standards of respect and dignity were compromised, undermining the legitimacy of discourse within Bebang’s digital community.
4.1.8.2. Case Study 2: Alexis.
Alexis’s withdrawal from sharing online indicates her lost opportunity for equal participation in digital discourse due to cyberbullying. The manipulated images and derogatory remarks likely misrepresented Alexis, challenging the validity of the claims made against her. The betrayal by friends highlights a lack of sincerity, as their actions did not reflect true intentions or feelings towards her. The actions against Alexis violated the ethical norms of honesty and integrity, calling into question the legitimacy of the discourse environment.
4.1.8.3. Case Study 3: Johnny.
Johnny felt silenced by the bullying, particularly as it exploited his vulnerability regarding depression, limiting his willingness to engage. The dissemination of his personal struggles as a form of ridicule twisted the truth about his condition for malicious purposes. The breach of trust from a friend reveals a profound insincerity in the communication within his social circle. Mocking someone’s mental health struggles grossly violates ethical standards of communication, lacking any form of legitimacy.
4.1.8.4. Case Study 4: Trixy.
The widespread cyberbullying across multiple platforms overwhelmed Trixy, forcing her to reconsider her online presence and silencing her voice. The name-calling and harassment likely included unfounded claims and insults, distorting the truth about her identity. The use of sexual harassment, especially from someone she knew, highlights a severe lack of sincerity and integrity in interactions. The malicious intent and spread of harassment clearly breach the normative rightness of ethical online communication.
4.1.8.5. Case Study 5: Brent.
The online adversity Brent faced hindered his ability to communicate freely, affecting his social interactions within academic circles. Adverse sentiments and rumors about the disagreement likely contained distortions or falsehoods challenging Brent’s reputation. The spreading of rumors and negative sentiments reflects a departure from truthful and sincere communication. The targeting of Brent, especially related to academic competition, undermines the legitimacy of ethical discourse among peers.
4.1.8.6. Case Study 6: Andrew.
Insulting language and criticisms restricted Andrew’s participation in social media, impacting his self-expression and communication. The cyberbullying Andrew experienced, based on personal insecurities, likely involved false narratives or exaggerated claims about his character. The deceitful nature of cyberbullying, exploiting personal vulnerabilities, underscores a lack of sincerity among online interactions. The toxic environment created by cyberbullying violates the ethical correctness expected in communicative actions.
4.1.8.7. Case Study 7: Rasheed.
Cyberbullying, based on unfounded allegations, restricted Rasheed’s ability to defend his academic integrity and engage in honest discourse. The accusations made against him distorted the truth, leveraging baseless claims for bullying purposes. The use of personal attacks for cyberbullying undermines the sincerity of communication, as actions were driven by envy rather than truth. The ridicule based on perceived personal relationships and orientation breaches the normative standards of respect and dignity in discourse.
4.1.8.8. Case Study 8: Marcus.
Encountering cyberbullying within a gaming community limited Marcus’s ability to express his viewpoints and engage with like-minded individuals. Conflict arising from differing viewpoints likely led to distortions of Marcus’s opinions, affecting the truthfulness of discourse within the community. During the bullying, Marcus faced questions about the sincerity of community interactions as disagreements escalated into personal attacks. The community’s failure to maintain a respectful discourse environment demonstrates a disregard for normative rightness in communication.
Habermas (1984)’s Theory of Communicative Action emphasizes the cooperative processes of individuals engaging in rational discourse. The key here is that specific criteria must be met for the communication to be truly rational. Through an analysis of the experiences of victims of cyberbullying, we gain an understanding of the many challenges they encountered, especially in relation to the principles of rational discourse. Each case reveals the impact of cyberbullying on violating Habermas’s principles, highlighting the disruption of an ideal discourse environment where individuals can communicate freely, truthfully, and with mutual respect.
-
Equal Opportunity for Speech Acts: Cyberbullying significantly hinders victims from participating in online discourse, effectively silencing them or severely limiting their engagement due to fear, shame, or social exclusion. This breach fundamentally undermines the democratic ethos of communicative action, which states that all should have an equal voice.
-
Truth: The spread of distorted truths and misinformation through cyberbullying challenges online discourse integrity. False narratives and exaggerated claims about victims distort the reality of their identities and actions, leading to misunderstandings and the spread of false information within digital communities.
-
Sincerity: The insincerity prevalent in cyberbullying—where bullies often hide behind anonymity to deceive, manipulate, or betray—erodes the foundation of trust necessary for meaningful discourse. The lack of genuine intention behind communications further alienates victims and disrupts the potential for authentic engagement.
-
Normative Rightness: Each case departs from ethical standards governing respectful interaction. By targeting individuals based on vulnerabilities, spreading unfounded allegations, or engaging in harassment, bullies flout the moral norms that should guide legitimate discourse. Such actions not only harm the individuals targeted but also corrupt the overall ethical climate of online spaces.
4.2. Key Themes Emerging from the Research
This section provides an overview of the main themes that have emerged from the data, shedding light on the intricate aspects of the research topic. Each theme is explored in detail, providing insights into the identified patterns and their ramifications.
4.2.1. Theme 1: Cyberbullying Characteristics and Dynamics
This theme represents the various features and patterns common to cyberbullying incidents. These characteristics are not limited to the individual actions or words of the bully, but extend to the broader social and technological context that facilitates this type of bullying.
Direct and indirect speech acts in cyberbullying refer to the use of both explicit (direct) and implicit (indirect) ways of conveying insults, threats, or derogatory remarks (Yule, 1996). Direct speech acts in cyberbullying might include explicit threats or insults, while indirect speech acts may involve implied insults, sarcasm, or passive-aggressive remarks. The bullies of Bebang use both direct and indirect methods to insult and undermine her. The direct method is evident in explicit insults, such as “Your personality belongs to the trash,” or “She is always asking for something but never gives back. Lord, take her away.” Indirect methods can be seen where the person being bullied is not directly named but is identifiable to those within the social group, such as in the case of Bebang with the “#Aling Bebang Problems” posts and the group chat created to backstab the victim.
Power imbalances in online interactions refer to the disparity in influence, control, or power between the bully and the target in online interactions (Chan et al., 2021). Power imbalance could be related to social status, popularity, knowledge of the online platform, or the ability to manipulate online narratives.
“The third time was when my friends made a group chat in Messenger without me. They made it as a medium for backstabbing. Peer influence did play a role as my cyberbullies took advantage of their spheres of influence in order to cause my other classmates to say bad things about me as well.” – Case 1
The bullies have the power in this narrative by dominating the narrative within the group chat, enabling them to subject her to ridicule without her awareness or means to defend herself. This secretive backstabbing, a type of interpersonal bullying, exploits the private nature of group chats. This demonstrates the ability of bullies to influence connections and reputations in private settings. Bullies employ strategic manipulation of their influence and social dynamics to intentionally isolate and specifically target the victim.
Social media platforms as avenues for bullying recognize that the platforms used for communication play a significant role in facilitating cyberbullying. This involves understanding how social media sites and chat groups can become venues for cyberbullying, and how their design or rules may either contribute to or mitigate cyberbullying.
“To sum everything up I was slandered for hooking up with my gay professor and that he does ‘service’ to me that’s why my grades are high and everything… They did on social media… A significant part of the bullying happened there by posting memes insinuating my identity and the things I ‘did’ there happened.” – Case 7
Social media platforms are powerful mediums for bullying, as exemplified by the encounter described in the case of Andrew. This led to the individual being publicly humiliated and subjected to cyberbullying. These platforms facilitate the rapid dissemination of harmful content by bullies, resulting in widespread damage to reputations that extend beyond the limitations of conventional bullying. Moreover, anonymity or pseudo-anonymity on these platforms can embolden bullies. This makes it easier to target individuals without immediate consequences.
4.2.2. Theme 2: Challenges to Authentic and Equal Online Conversations
This theme explores how power dynamics, misunderstandings, and the suppression of genuine communication hinder the possibility of achieving open and fair dialogue online. It examines the barriers that prevent individuals from engaging freely and equally in social media.
Suppression of authentic communication: Fear of cyberbullying leads to self-censorship on social media, with individuals hesitant to share honest opinions or personal stories.
“I go to the extent of creating Facebook and Gmail accounts without using my real name. Thinking it is the new me. Creating that so-called new identity in social media gives me peace of mind that nobody knows me, and so they can’t judge me.” – Case 2
Influence of power dynamics in online interaction can significantly influence the course of conversations. Accounts with a substantial following or backed by institutions can exert an overwhelming influence, overshadowing less popular viewpoints.
“I was cyberbullied by a single person in college due to a disagreement in thesis grouping. Forms of cyberbullying I have experienced are spreading rumors, shooting threat post and a form of ‘Appeal to Pity’ social media posting to make me look bad to our mutual friends and classmates. The experience reduced my circle of friends in college to about half, almost all of my friends from the other section (where he is close with) are scared to talk to me or even look at me because the bully specifically told them that if they are friends with me then they should leave the friends group or group-chat (I was sent a screenshot from a close friend of mine in the other section) where I knew that information.” – Case 3
Role of misunderstandings lies in the potential for misinterpretations of online content to rapidly escalate into cyberbullying events, as conflicts deepen quickly owing to the viral nature of social media.
“The second time I was cyberbullied was when there was a misunderstanding between me and a friend. That misunderstanding became a focal point and he started with gc (group chat). He didn’t explicitly mention my name however, within the classroom, it was already well-implied. He also proceeded to post about me in to insult me in Facebook.” – Case 1
Barriers to fair, constructive, and open communication: Any element that hinders equitable and balanced communication prevents all parties from participating equally and openly. The dynamics within a group might impede equitable and inclusive discussions, with some voices being marginalized or silenced. Cyberbullying encompasses aggressive and deceptive strategies that disrupt constructive online dialogue, substituting it with damaging interactions.
4.2.3. Theme 3: Consequences of Inauthentic Communication and Power Imbalance on Online Interaction
Emotional and psychological impact due to suppression of authentic communication emphasizes the psychological consequences of cyberbullying on mental health. When someone’s capacity to express themselves genuinely is suppressed, it can result in notable emotional and psychological anguish.
“The bullying gave me some sort of anxiety… It just feels like I am existing in a place where I shouldn’t exist at all.” – Case 6
Erosion of self-esteem and self-perception due to disruptive power dynamics highlights how cyberbullying can erode an individual’s self-esteem and self-image. Victims, when confronted with power imbalances and aggressive interactions, may begin to absorb the negative messages they receive.
Behavioral changes as a reaction to inauthentic online interaction primarily revolve around the consequences of cyberbullying on its victims, causing them to modify their conduct to prevent additional harm. These adjustments often involve strategies that limit authentic self-expression, therefore reducing meaningful social interactions.
“I developed a bipolar disorder and needed to take counseling and therapy regardless of all the coping strategies I developed through the years.” – Case 5
Impacts on personal relationships due to violations of rational online interaction focus on the impact that cyberbullying can have on relationships between individuals. Trust issues frequently arise as a substantial result of the betrayal and deception seen in cyberbullying incidents (Woodluck et al., 2023).
Responses to unequal opportunities in online interaction: Victims or bystanders may alter their online interactions or silence their voices to avoid becoming targets. This reflects imbalances in who gets heard or attacked online.
This approach reflects a coping mechanism where the victims modify their online behavior—here, by adopting alternate identities—to prevent becoming a target again. It highlights how the fear of cyberbullying can lead individuals to conceal their true selves, seeking safety in anonymity or diversified online personas. This strategy is a direct consequence of the imbalances in digital spaces, where not everyone feels equally safe or heard, driving them to find alternative ways to express themselves while minimizing the risk of harassment.
4.2.4. Theme 4: Navigating Authenticity and Resilience in Adverse Online Settings
This theme explores the resilience of individuals facing cyberbullying. It discusses strategies for adapting one’s identity for safety and comfort, varying responses to cyberbullying from avoidance to confrontation, and the journey toward healing from such experiences. Finally, it delves into the recovery journey to highlight the importance of support systems in overcoming the emotional scars left by cyberbullying, aiming for a return to emotional and psychological health.
Strategies for expressing oneself in adverse settings primarily revolve around how victims maintain, regulate, or hide their true selves to function or protect themselves within hostile or unfavorable circumstances. These strategies often involve constructing different identities or personas, adopting pleasing behaviors, or limiting one’s presence or visibility within the space. Such strategies help them navigate and negotiate the pressures and expectations within the environment, which could often suppress or discourage their authentic expression.
“I have forgiven the bullies even though they never asked for apologies. But I would always hold on to what I learned from it… I communicate with caution especially when the conversation goes personal level.” – Case 2
Coping and confrontation strategies in cyberbullying delves into the various strategies and techniques used by victims to deal with instances of cyberbullying. These methods range from avoidance tactics to direct confrontation, to speaking up. Unfortunately, this can also include harmful coping mechanisms.
“Personally, it was hard to cope up. There were sleepless nights. And I lay low from social media. I made private different social media accounts for people I know very well and that I trust. As for my body shamers. They made me go on a diet. It was healthy for my body but the pressure to have a body that everyone would approve of is challenging mentally. My friends told me not to over do it because people will always have something to say. As for the sexual harassment. I ignored those people because they used dummy accounts. But after quite a while. I did speak up through tweets about the experience. It was already too much for me. I did not want to send them the wrong signal that my silence means an acquiescence. So, when I tweeted about it, other girls I didn’t know shared their experience as well. They retweet and support me. Their sharing of experience helped me realize that the problem is not me but those people who abuses other people online…” – Case 4
The recovery journey pertains to the steps and actions taken by individuals to heal and regain their emotional and psychological well-being following a traumatic or adverse cyberbullying experience. This process often involves seeking and receiving support from others, whether they are close friends, family, or professionals.
“.. I took a notebook to write what is my life’s purpose, wrote a goal, and started living in a new direction. I am intentional in everything I do. I stopped crying the moment I defined my worth, not by my bullies’ words.” – Case 2
Building resilience and personal growth encompasses the process that cyberbullying victims undergo as they cultivate resilience, self-sufficiency, and personal development despite the difficulties and violations they encounter in social media. It emphasizes overcoming trauma, adopting healing techniques, developing coping mechanisms for future situations, and the unforeseen personal growth that can arise from such challenging experiences.
4.2.5. Theme 5: Empowering Online Communities Through Support and Education
This theme reflects that community support, appropriate technological interventions, and literacy are integral to upholding the principles of equal participation, sincerity, truth, and normative rightness in digital communication. These elements help create a space where people can engage in a reasonable, respectful, and genuine way, as suggested by Habermas’s concept of ‘communicative rationality.’ It is about making sure conversations are open, fair, and honest.
Fostering community and social support not only provides immediate comfort but also sets the foundation for enduring resilience and recovery, emphasizing the necessity of both professional guidance and a strong personal support network in navigating the aftermath of cyberbullying. Creating a supportive online environment where individuals feel connected and supported by others is equally important and will offer members a sense of belonging and safety. Through shared experiences, advice, and emotional support, these communities can significantly mitigate the negative impacts of cyberbullying, promoting resilience and well-being among affected individuals.
“I only turn to my closest best friends for support and to be heard but all other stuff needs to be faced by me… I’ve been talking to the guidance counselor.” – Case 1
Addressing challenges and leveraging technological interventions involves the hope of developing and implementing technology-based solutions such as filtering software, reporting mechanisms, and educational apps to help detect, prevent, and respond to online harassment. These interventions aim to empower users, providing them with resources to protect themselves and others from cyberbullying.
“The best way cyberbullying can be prevented is if they realize the cost of negative content and how it can affect its viewers… AI can track and flag someone for saying a pattern of offensive things [and] can help detect and be flagged sent by a warning.” – Case 6
Advocacy for awareness and education programs emphasizes promoting knowledge and preventive measures against cyberbullying through targeted educational programs and campaigns. This can raise awareness among Internet users of all ages about the dangers of cyberbullying, the importance of digital etiquette, and how to safely navigate online spaces.
4.3. Cyberbullying and Social Media Platforms
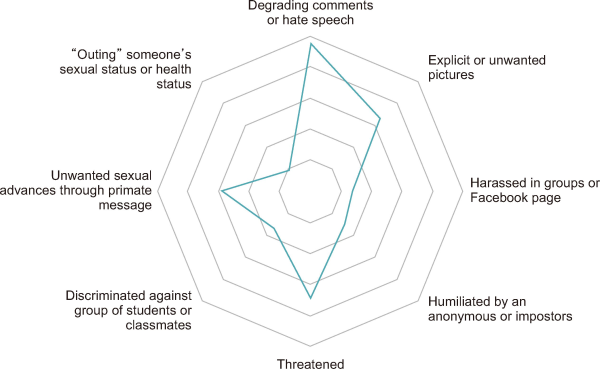
The survey results from the three universities reveal a concerning spectrum of cyberbullying behaviors (Fig. 3). Degrading comments or hate speech was most common at 23.8%, followed by threats (17.2%), and unwanted sexual messages (14.5%). Other types included sharing unwanted pictures (16.3%), discrimination (8.4%), and impersonation (7.9%). Group harassment and ‘outing’ someone’s private information were less common but still reported. This highlights the need for better online safety and respect across social media platforms.
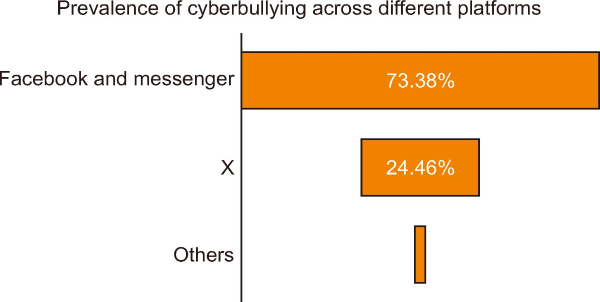
Facebook and Messenger (73%) are the primary mediums used where cyberbullying occurs, while platform X accounts for 25% of cyberbullying cases (Fig. 4).
This study’s exploration of eight cases reveals the dual nature of social media platforms such as Facebook and its Messenger feature (Fig. 5), which have become conduits for cyberbullying despite their intent to foster connections. These platforms have been misused for anonymous harassment, leading to lasting emotional distress. Facebook’s design and group features exemplify how they can enable the dissemination of misinformation and malicious personal assaults, thus weakening the integrity of respectful and authentic communication. This situation necessitates a collaborative endeavor to advocate for digital empathy, accountable online conduct, and platform regulations that reduce cyberbullying to establish a safer and more inclusive digital atmosphere.
The analysis of the cases reveals how IT platform features and dynamics on social media can either facilitate or impede speech acts characteristic of cyberbullying. The characteristics of these IT platforms can significantly influence the prevalence and nature of cyberbullying incidents:
Visibility and Virality: Due to social media’s quick information distribution, offensive speech activities may spread more quickly. Bullying’s effects can be amplified by information that spreads rapidly, as was the case in Andrew’s case when false rumors spread to a large audience. Bullies may target more people since it is so simple to share content, which worsens the damage they do.
Amplification of Power Imbalances: Platform structures and algorithms can magnify the influence of certain users over others. Features such as trending topics, like and share mechanisms, and visibility algorithms can disproportionately elevate the voices of those with large followings or those who manipulate content for broader dissemination. This dynamic can exacerbate cyberbullying, misinformation, and other forms of online harm, as it allows dominant voices to overshadow or silence less powerful individuals.
Anonymity and Pseudonymity: Cyberbullying may be made more accessible by the option to post anonymously or use a pseudonym, since it gives offenders a sense of anonymity and allows them to use hurtful comments without worrying about being identified. This anonymity may give bullies the confidence to propagate untrue information, launch personal assaults, and use disparaging language. On the other hand, platforms that demand genuine names may prevent such speech actions by enhancing responsibility and lowering the possibility of bullying motivated by anonymity.
Privacy Controls: Cyberbullying may be stopped by features that let users manage their privacy settings and control who can view their material. The usage of private settings demonstrates how privacy measures may prevent bullies from getting access to sensitive material. By limiting visibility, bullies may have fewer opportunities to target their victims.
This study highlights how social media’s features can influence cyberbullying, aligning with Habermas’s conditions for rational discourse: truth, non-coercion, sincerity, and normative rightness. The quick spread of misinformation challenges the truth. Power imbalances and anonymity can create a coercive environment, limiting free speech. Misleading stories and tactics undermine sincerity. The absence of universal respectful norms hampers normative rightness. These findings emphasize the need for platforms to foster environments that discourage cyberbullying and promote respectful, truthful, and free communication, supporting a healthier digital space.
5. DISCUSSION
Cyberbullying, an adverse product of the digital age, represents a complex and detrimental issue affecting individuals worldwide, particularly adolescents and young adults (Chisholm, 2014; Hendry et al., 2023; Peled, 2019; Stewart et al., 2014). The characteristics and dynamics of cyberbullying shape its manifestation and impact, making it a unique form of harm that extends beyond traditional bullying (Bauman et al., 2013). Critical characteristics of cyberbullying include anonymity, publicity, persistence, and accessibility, all of which are inherent in digital platforms (Wachs et al., 2019). These attributes contribute to the pervasiveness and intensity of online bullying, often exacerbating the damage inflicted on the victims (Stewart et al., 2014). Simultaneously, the dynamics of cyberbullying encompass power imbalances, role switching, the bystander effect, and rapid escalation, elements that can complicate its resolution and intensify the psychological harm to those involved (Saif & Purbasha, 2023; Wong-Lo & Bullock, 2014).
5.1. Strategic Approaches to Mitigating Cyberbullying
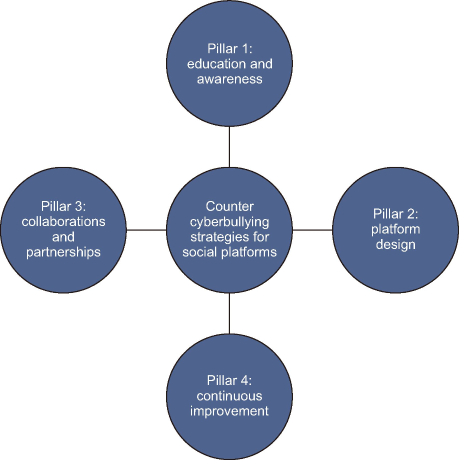
To address the issue of cyberbullying on social media, implementing a strategy that understands today’s online behavior and fundamental tenets of effective communication is necessary. This involves examining how people interact online today and combining that with fundamental communication principles. Drawing on Habermas’s principles, a pillar is proposed (Fig. 6) to foster a digital environment where genuine, rational, and enriching interactions prevail, contributing to more respectful and enriching interactions.
-
Education and Awareness: Central to combating cyberbullying is enhancing users’ digital literacy, highlighting cyberbullying’s consequences, and fostering a culture of respect online. This initiative calls for comprehensive education programs that employ case studies and discussions on ethical online behavior.
-
Platform Design: Social media platforms must prioritize user safety through design innovations. This includes intuitive reporting mechanisms and advanced content moderation technologies that deter harmful behavior alongside promoting transparency and accountability in moderation practices.
-
Partnerships for Collective Action: Collaboration with educational institutions, NGOs, and law enforcement can expand the reach and impact of anti-cyberbullying initiatives. These partnerships should facilitate open dialogue and constructive engagement in line with the principles of communicative action.
-
Commitment to Continuous Improvement: An iterative approach to strategy enhancement, guided by user feedback and ongoing research, is crucial. This ensures adaptability in response to the evolving nature of cyberbullying and digital interaction patterns.
5.2. Theoretical and Practical Implications of Study Findings
The implications of our findings extend into both theoretical and practical domains. The study underscores the critical need for governance models on social media that foster meaningful participation and dialogue (McCarthy et al., 2023), emphasizing the role of ethical communication in platform policies. Furthermore, the success of interventions in various contexts highlights the potential of integrated, theory-based approaches to mitigate cyberbullying effectively (Barlett, 2023; Özgür, 2020).
To address cyberbullying and foster a culture of respect and understanding online, it is crucial to prioritize ethical involvement and mutual respect, which are key principles of discourse ethics. Adapting discourse ethics for digital platforms emphasizes ethical conduct within online learning communities and provides a roadmap for creating digital environments where constructive and respectful discourse can flourish (Luppicini, 2009).
Our research uncovers insights into the dynamics of digital communication, primarily focusing on the challenges and potential pathways forward in addressing cyberbullying. It illustrates how online communication can differ from face-to-face interaction, with anonymity and the digital space presenting new challenges. It also highlights a growing online aggression culture, reflecting broader societal issues. The blending of online and offline lives, as seen in personal experiences, suggests a close connection between the digital and physical worlds. While our study has primarily focused on the disruptive impact of cyberbullying within digital communications, it is essential to acknowledge the existence of online communities and interactions where rational discourse thrives. These positive examples serve as guiding lights, showcasing the capacity of online platforms to foster environments conducive to informed, respectful, and productive conversations. Platforms that incorporate design features encouraging transparency, accountability, and mutual respect among users significantly contribute to the prevalence of such rational discourse.
The theoretical implications reaffirm Habermas’s theory’s applicability in analyzing the complexities of digital communication, as shown in Table 5.
Table 5
Theoretical implications of the research study
| Summary of findings | Rational discourse |
Theoretical implication confirming the theory |
|---|---|---|
| Victims encountered limitations in their capacity to speak on social media as a result of unrestricted coercive actions. This generally indicates how the use of coercion in online environments may significantly limit open and sincere communication | Non-coercion | The results obtained from participants’ accounts prove that coercion substantially impacts authentic communication. These observations highlight the significance of maintaining discourse without coercion to promote genuine online relationships. This emphasizes the need to establish digital platforms where people can interact openly and truthfully without the worry of being forced or manipulated, in keeping with theoretical viewpoints that stress the significance of non-coercive communication for meaningful online interactions |
| The victims encounter challenges related to truthfulness. False accusations, misleading information, and misunderstandings frequently distort reality and often distort the truth, resulting in unfair persecution and the dissemination of baseless narratives. These problems emphasize the widespread challenge of finding the truth online, where the ability to remain anonymous and spread false information can significantly harm individuals’ reputations and relationships. This underlines the theory’s emphasis on the necessity of truth for genuine communication and vigilance against falsehoods to ensure integrity in online interactions | Truth | The accounts provided by participants underscore the crucial significance of truth in facilitating effective communication, validating the theory that prioritizes truth as a fundamental element for genuine discussion. These concrete instances demonstrate the frequent presence of disinformation and deception in online discussions, providing practical observations on the pervasive problem of distorting truth in digital exchanges. This highlights the theory’s focus on the importance of truth for authentic communication and the requirement to be cautious of falsehoods to maintain integrity in online interactions |
| The various testimonies from individuals experiencing cyberbullying expose the complex significance of sincerity in online interactions. Victims encounter difficulties discerning genuine motives because of the insincerity and anonymity provided by the Internet. Some employ passive techniques that emphasize the need for sincerity in resolving conflicts, while others confront the deceitfulness of their peers, which dramatically contrasts with their own genuineness. Bullies manipulate deceitfulness to benefit themselves, emphasizing the crucial role of genuineness in the cyberbullying dynamic and its consequences. These cases highlight the challenges and importance of maintaining authenticity and integrity in digital spaces | Sincerity | The varied encounters of participants with cyberbullying reinforce the theoretical significance of sincerity in effective communication. These experiences illuminate how the anonymity inherent in social media complicates the preservation of sincerity, affecting the integrity of online interactions. This situation underscores the need for strategies that enhance sincerity in digital platforms, ensuring that the quality of discourse is not compromised by the challenges posed by online anonymity |
| The stories of cyberbullying victims highlight the crucial role of fairness and respect online. Their fight for justice is often undermined by a lack of support from their online communities, pointing to a failure to maintain a sense of unity and solidarity. Experiences of exclusion and harassment question the fairness of online social dynamics and challenge the societal norms that govern our interactions, revealing a tension between personal authenticity and group expectations. These incidents expose an apparent disregard for equality and respect, essential for ethical and just interactions in digital spaces | Normative rightness | The experiences shared by participants underscore the critical importance of normative rightness in shaping online interactions, as posited by the theory. These real-world insights reveal how digital spaces can either support or undermine established social norms, stressing the importance of fostering an online environment that is both equitable and respectful. This calls for concerted efforts to reinforce normative principles in digital communication, ensuring that online exchanges are guided by fairness and respect for societal standards |
Practically, there is a call for digital etiquette education and targeted support for cyberbullying victims. Policy implications suggest stricter cyberbullying laws, mandated platform regulation, and digital literacy in educational curricula. Our study emphasizes the importance of using diverse and well-informed strategies to address cyberbullying, which aligns with the broader discussion on digital ethics and platform governance. This entails dealing with the technological components of cyberbullying and actively involving oneself in the socio-cultural aspects of digital engagement.
5.3. Study Limitations and Future Directions
This study’s applicability to all cyberbullying cases may be limited due to the unique contexts affecting individuals’ experiences. While focused on cyberbullying among college students on social media through the Communicative Action Theory framework, future research should further examine strategies for creating a secure online environment and the roles of educational institutions and social media platforms in mitigating cyberbullying. Additionally, exploring the influence of bystanders and the broader online community could enhance our understanding of cyberbullying dynamics.
This groundwork paves the way for future inquiries into the nuances of cyberbullying within the digital landscape, emphasizing the importance of digital etiquette education, victim support, and legislative measures for a safer online environment. Harnessing the potential of online platforms for constructive discourse is essential for fostering inclusive and healthy digital communities.
6. CONCLUSION
The instances of cyberbullying observed on social media platforms clearly differ from Habermas’s envisioned rules of rational discourse. Cyberbullying often involves coercion, where victims are pressured or forced into silence or compliance through aggressive online behaviors. This directly undermines the principle of non-coercion, which is crucial for genuine discourse. Furthermore, the spreading of distorted truths—a hallmark of cyberbullying—violates Habermas’s emphasis on sincerity and the foundational role of truth in discourse. Insincerity is further facilitated by the cloak of online anonymity, allowing perpetrators to hide their true identities while engaging in deceitful actions that disrupt the mutual trust necessary for rational communication. Violations of ethical correctness, observed in cyberbullies’ malicious intent and actions, further exemplify the departure from Habermas’s principles. Such behaviors erode the normative foundation of discourse ethics, which demands respect for the dignity and autonomy of all participants in communication. These elements—coercion, spreading distorted truths, insincerity, and ethical violations—collectively indicate a significant divergence from the ideal conditions for reasoned, respectful, and productive communication, as outlined by Habermas.
Given this, it becomes evident that cyberbullying represents not just a failure to adhere to the norms of rational discourse, but also a challenge to the very possibility of such discourse in digital spaces. This underscores the importance of developing strategies, both at the level of platform design and through educational interventions, that can foster environments conducive to Habermas’s ideals. It is essential for future research to not only continue shedding light on the complexities of cyberbullying, but also to explore innovative ways to cultivate digital communities where rational discourse can thrive.
REFERENCES
, , , (2017) School performance, social networking effects, and learning of school children: Evidence of reciprocal relationships in Abu Dhabi Telematics and Informatics, 34(8), 1433-1444 https://doi.org/10.1016/j.tele.2017.06.006.
(2023) Cyberbullying as a learned behavior: Theoretical and applied implications Children (Basel, Switzerland), 10(2), 325 https://doi.org/10.3390/children10020325.
, , (2013) Associations among bullying, cyberbullying, and suicide in high school students Journal of Adolescence, 36(2), 341-350 https://doi.org/10.1016/j.adolescence.2012.12.001.
(1995) Business communications modelling: Performative vs informative IFAC Proceedings Volumes, 28(7), 423-428 https://doi.org/10.1016/S1474-6670(17)47142-4.
, , (2021) Cyberbullying on social networking sites: A literature review and future research directions Information and Management, 58(2), Article 103411 https://doi.org/10.1016/j.im.2020.103411.
, , (2017) A meta-analysis of factors predicting cyberbullying perpetration and victimization: From the social cognitive and media effects approach New Media & Society, 19(8), 1194-1213 https://doi.org/10.1177/1461444816634037.
(2014) Review of the status of cyberbullying and cyberbullying prevention Journal of Information Systems Education, 25(1), 77-87 https://jise.org/volume25/n1/JISEv25n1p77.pdf.
, , (2021) Identification of key cyberbullies: A text mining and social network analysis approach Telematics and Informatics, 56, 101504 https://doi.org/10.1016/j.tele.2020.101504.
(2019) Cyberbullying practices and experiences of the Filipino college students' social media users Journal of Educaction, Management and Social Sciences, 2(1), 43-51 https://scholar.google.com/scholar?oi=bibs&hl=en&cluster=9646104241615606092.
, , (2015) Learning from traditional bullying interventions: A review of research on cyberbullying and best practice Aggression and Violent Behavior, 23, 61-68 https://doi.org/10.1016/j.avb.2015.05.009.
, , , , , , , , , , , , , , (2020, November 23-27) Proceedings of the 28th International Conference on Computers in Education Asia-Pacific Society for Computers in Education Peer influence, risk propensity and fear of missing out in sharing misinformation on social media during the COVID-19 pandemic, 351-359
, , , , , , (2023) Cyberbullying among children and youth in Türkiye: A systematic review and meta-analysis Journal of Pediatric Nursing, 73, 184-195 https://doi.org/10.1016/j.pedn.2023.09.003.
, , , (2021) Cyberbullying among adolescents in Egypt: A call for correlates with sense of emotional security and psychological capital profile Journal of Pediatric Nursing, 61, E99-E105 https://doi.org/10.1016/j.pedn.2021.05.008.
, , , (2023) Cyberbullying research in Canada: A systematic review of the first 100 empirical studies Aggression and Violent Behavior, 69, 101811 https://doi.org/10.1016/j.avb.2022.101811.
, , (2016) Associations between social media and cyberbullying: A review of the literature mHealth, 2, 46 https://doi.org/10.21037/mhealth.2016.12.01.
, , , (2023) Recommendations for cyberbullying prevention and intervention: A Western Canadian perspective from key stakeholders Frontiers in Psychology, 14, 1067484 https://doi.org/10.3389/fpsyg.2023.1067484.
, (2010) Bullying, cyberbullying, and suicide Archives of Suicide Research, 14(3), 206-221 https://doi.org/10.1080/13811118.2010.494133.
(2010) The logic of qualitative survey research and its position in the field of social research methods Forum: Qualitative Social Research, 11(2), Art. 11 http://nbn-resolving.de/urn:nbn:de:0114-fqs1002110.
, , , (2023) The dark side of digitalization and social media platform governance: A citizen engagement study Internet Research, 33(6), 2172-2204 https://doi.org/10.1108/INTR-03-2022-0142.
(2019) The rise of social media https://ourworldindata.org/rise-of-social-media
(2020) A systematic review on cyberbullying interventions and preventions Shanlax International Journal of Education, 9(1), 11-26 https://doi.org/10.34293/education.v9i1.3373.
, (2006) Bullies move beyond the schoolyard: A preliminary look at cyberbullying Youth Violence and Juvenile Justice, 4(2), 148-169 https://doi.org/10.1177/1541204006286288.
(2019) Cyberbullying and its influence on academic, social, and emotional development of undergraduate students Heliyon, 5(3), e01393 https://doi.org/10.1016/j.heliyon.2019.e01393.
, (2011) Habermas and information systems research: New directions Information and Organization, 21(3), 123-141 https://doi.org/10.1016/j.infoandorg.2011.06.001.
, (2023) Cyberbullying among youth in developing countries: A qualitative systematic review with bibliometric analysis Children and Youth Services Review, 146, 106831 https://doi.org/10.1016/j.childyouth.2023.106831.
, , , (2022) Systematic literature reviews in cyberbullying/cyber harassment: A tertiary study Technology in Society, 70, 102055 https://doi.org/10.1016/j.techsoc.2022.102055.
, , , , (2014) The development and psychometric investigation of the cyberbullying scale Journal of Interpersonal Violence, 29(12), 2218-2238 https://doi.org/10.1177/0886260513517552.
(2004) The online disinhibition effect CyberPsychology & Behavior, 7(3), 321-326 https://doi.org/10.1089/1094931041291295.
, , , , (2022) The current status of cyberbullying research: A short review of the literature Current Opinion in Behavioral Sciences, 46, 101152 https://doi.org/10.1016/j.cobeha.2022.101152.
, , (2019) Understanding the overlap between cyberbullying and cyberhate perpetration: Moderating effects of toxic online disinhibition Criminal Behaviour and Mental Health, 29(3), 179-188 https://doi.org/10.1002/cbm.2116.
(2007) The authority and responsibility of school officials in responding to cyberbullying Journal of Adolescent Health, 41(6 Suppl 1), S64-S65 https://doi.org/10.1016/j.jadohealth.2007.08.013.
, (2014) Digital metamorphosis: Examination of the bystander culture in cyberbullying Aggression and Violent Behavior, 19(4), 418-422 https://doi.org/10.1016/j.avb.2014.06.007.
, , , (2023) "Living in the darkness": Technology-facilitated coercive control, disenfranchised grief, and institutional betrayal Violence Against Women, 29(5), 987-1004 https://doi.org/10.1177/10778012221114920.
, (2021) Towards descriptive adequacy of cyberbullying: Interdisciplinary studies on features, cases and legislative concerns of cyberbullying International Journal for the Semiotics of Law, 34(4), 929-943 https://doi.org/10.1007/s11196-021-09856-4.
- Submission Date
- 2023-01-08
- Revised Date
- 2024-03-27
- Accepted Date
- 2024-04-21